Women's fashion. All Home & Living. Home Bath & Beauty Pet Supplies. Hand Line Drawing Print uk, Holding Hands Line Art Poster, Hands line art, Line art poster, Line art print, Black white print, Womans line ChloeElizabethPrints 4.5 out of 5 stars (45) $ 5.08. Add to Favorites. One really great way to explore line quality in fashion drawing, aside from the pencil/ charcoal route, is getting nitty-gritty with what is available in felt and brush-tip pens, which I always have in my creative and professional studio kit! I Draw Fashion shows you how to draw fashion sketches for beginners. Illustrated step-by-step tutorials, drawing tips, free croquis and body templates. How to draw fashion figures How to draw clothes, fabrics and patterns Fashion design contests and more. Improve your skills & create unique fashionable drawings! All fashion drawings consist of lines, curves, and geometric shapes. Figuring out how to draw smooth, flowing lines and shapes that vary from dark to light, thick to thin, and bold to subtle isn't always easy. Fortunately, practice really does make perfect, so the more you draw. Line drawing fashion. Mar 25, 2021 - Explore Rania Maged's board 'Art - Line drawing', followed by 761 people on Pinterest. See more ideas about line drawing, art, drawings.
I was just setting up my AWS CLI on a new Windows 10 machine and I ran into this error when trying to remote into my EC2 instance.
Currently, we accept online payments through PayPal or FastSpring service. Using the FastSpring system you can pay by credit/debit card, PayPal, Amazon and other payment methods. If you cannot use PayPal or FastSpring for some reason – contact one of our resellers. We can also send you an invoice for the bank transaction. Universal Database Tool Free multi-platform database tool for developers, database administrators, analysts and all people who need to work with databases. Supports all popular databases: MySQL, PostgreSQL, SQLite, Oracle, DB2, SQL Server, Sybase, MS Access, Teradata, Firebird, Apache Hive, Phoenix, Presto, etc.

This is not related to AWS in any shape or form – it is a straightforward SSH requirement that is enforced on both Windows and Unix systems.

You now have a public and private SSH key pair you can use to access remote. The first thing we are going to solve using this config file is to avoid. SSH clients will typically use /.ssh/identity (ssh v1) or one of /.ssh/idrsa or /.ssh/iddsa (v2) as the default private key. You can change this in /.ssh/config (the IdentityFile parameter - the -i option to SSH actually overrides this. See man sshconfig for details).
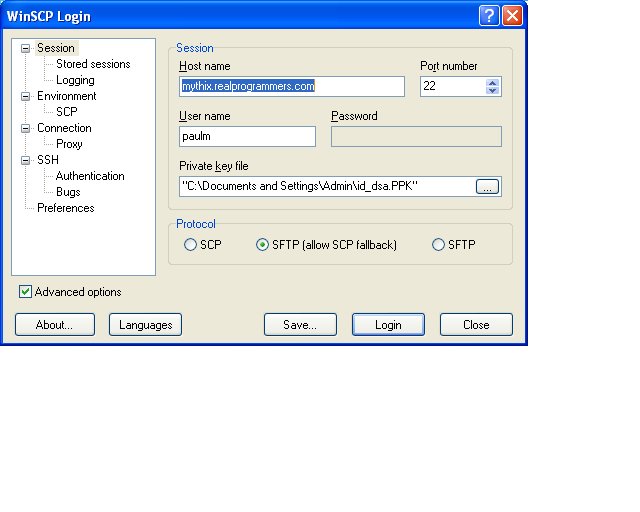
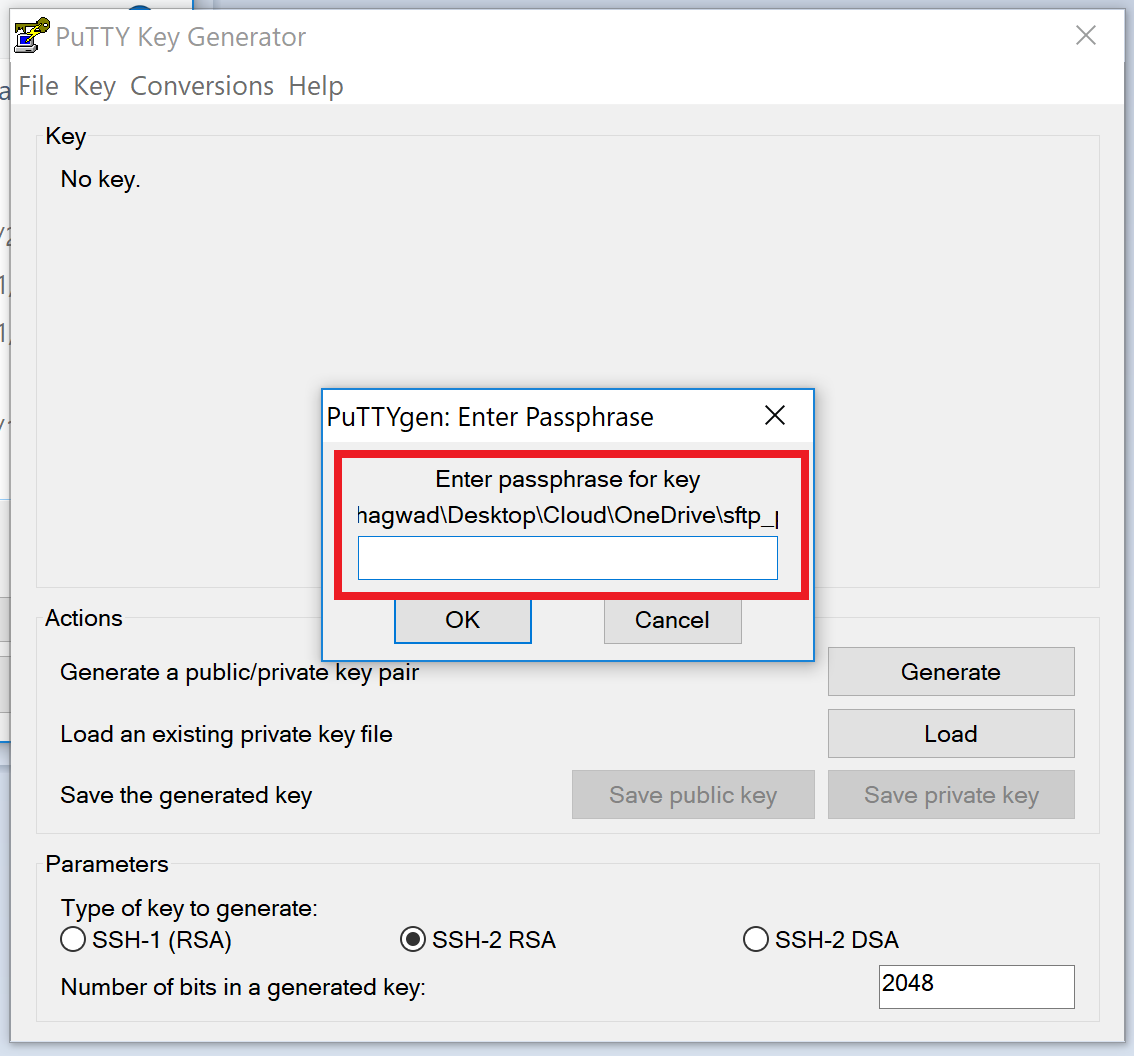
To perform private key authentication, you will also need the passphrase, which together with the private key, will allow authentication. What is really needed is for RenciSSH to get with the times and write a publickeyauthentication method. Overview Public key authentication is a way of logging into an SSH/SFTP account using a cryptographic key rather than a password. $ ssh-keygen On execution, we are prompted to specify a file in which to save the private key, the default being /home/user/.ssh/idrsa; here idrsa is the name of our Private Key file. You can always specify a different path and name for the Private Key file. For our demonstration, we shall use the default configuration.
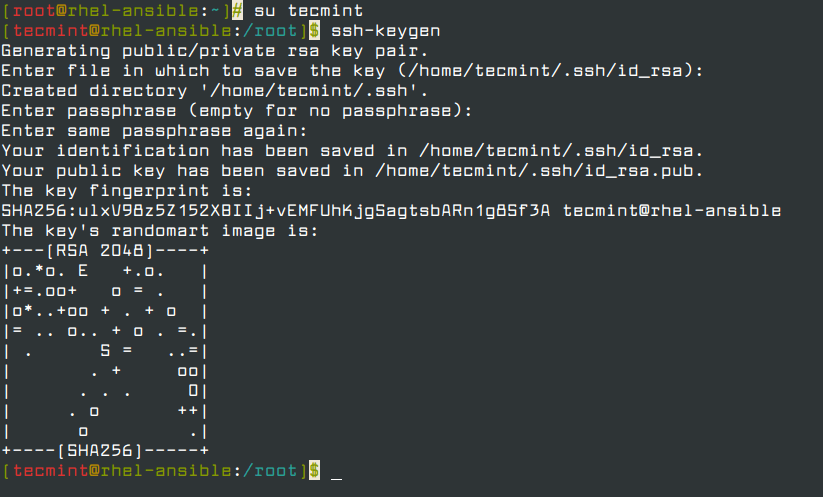
The issue is that we haven't protected our private key file so if we're going to use it to connect to an SSH endpoint then the OS forces us to conform to security standards by flagging up that UNPROTECTED PRIVATE KEY FILE error.
The solution is simple – we must fix exactly what it tell us to do in those bold capital letters. So let's fix the security settings for our file.

The private key file that I'm trying to use as you may see from the screenshot is 'ec2-demo.pem'. So we start by finding it in Windows Explorer.
now right-click on it and go to 'Properties' and then the 'Security' tab and then click on 'Advanced'.
Linux Ssh Use Private Key
On the Advanced tab we need to do the folowing:
Ssh Use Private Key Files
- Make sure that you, the user who is logged in, is the file owner
- Disable inheritance. If it prompts you to remove all current inherited permissions then accept it.
- We need to give us Full Control. First, make sure that the Permission Entries panel is empty, i.e. there are no explicit permissions set. Then click on Add, then click on Select a Principal at the top and then click on 'Advanced' and use 'Find Now' to find the user you are logged in as. Once you find it, tick the Full Control box and click ok.
This is not related to AWS in any shape or form – it is a straightforward SSH requirement that is enforced on both Windows and Unix systems.
You now have a public and private SSH key pair you can use to access remote. The first thing we are going to solve using this config file is to avoid. SSH clients will typically use /.ssh/identity (ssh v1) or one of /.ssh/idrsa or /.ssh/iddsa (v2) as the default private key. You can change this in /.ssh/config (the IdentityFile parameter - the -i option to SSH actually overrides this. See man sshconfig for details).
To perform private key authentication, you will also need the passphrase, which together with the private key, will allow authentication. What is really needed is for RenciSSH to get with the times and write a publickeyauthentication method. Overview Public key authentication is a way of logging into an SSH/SFTP account using a cryptographic key rather than a password. $ ssh-keygen On execution, we are prompted to specify a file in which to save the private key, the default being /home/user/.ssh/idrsa; here idrsa is the name of our Private Key file. You can always specify a different path and name for the Private Key file. For our demonstration, we shall use the default configuration.
The issue is that we haven't protected our private key file so if we're going to use it to connect to an SSH endpoint then the OS forces us to conform to security standards by flagging up that UNPROTECTED PRIVATE KEY FILE error.
The solution is simple – we must fix exactly what it tell us to do in those bold capital letters. So let's fix the security settings for our file.
The private key file that I'm trying to use as you may see from the screenshot is 'ec2-demo.pem'. So we start by finding it in Windows Explorer.
now right-click on it and go to 'Properties' and then the 'Security' tab and then click on 'Advanced'.
Linux Ssh Use Private Key
On the Advanced tab we need to do the folowing:
Ssh Use Private Key Files
- Make sure that you, the user who is logged in, is the file owner
- Disable inheritance. If it prompts you to remove all current inherited permissions then accept it.
- We need to give us Full Control. First, make sure that the Permission Entries panel is empty, i.e. there are no explicit permissions set. Then click on Add, then click on Select a Principal at the top and then click on 'Advanced' and use 'Find Now' to find the user you are logged in as. Once you find it, tick the Full Control box and click ok.
Close all windows and try running your SSH command again. It should work now.
Ssh Specify Private Key File
If it doesn't, here's the check list: double check that you are the owner of the file, that you have Full Control permissions assigned and finally that there are no other permissions set except the one giving you full control.

